Autoenrollment Connector : Interaction with Windows
Introduction
This page describes the installation procedure of the active directory and the different configuration steps that must be performed, to interact with the MTG Autoenrollment Connector (AEC). It shows the process of a clean installation, for the purpose of using the AEC, and focuses on the interaction between the Windows components and the AEC.
Several steps may have already been performed in your organization (e.g., some components may already be installed). Deviations from real-world installations are expected.
| This page serves descriptive purposes only and is not a replacement to guides on installing/securing/hardening an active directory, configuring DNS and other administrative actions. It is meant as assistance to an administrator for the configuration of Windows systems to use the AEC. |
| Security and hardening aspects of the installation and configuration of Windows components are not covered in this page. Security warnings shown in screenshots must be addressed in real-world installations. |
Overview
Existent Active Directory Installation includes the requirements on an existing active directory installation and which data should be configured at the AEC.
In Active Directory Installation the active directory installation procedure is described. Additionally, included are the process to promote it to a domain controller as well as the installation of Certification Authority Management Tools.
User Management describes the process of creation and configuration of Windows users that are necessary for the AEC to function properly.
Computers briefly treats the configuration of AEC as a service and computer that can be accessed from a Windows domain.
AEC provides the necessary configuration of AEC for the examples in this page.
Configure Templates shows the configuration of certificates templates and discusses the Autoenrollment configuration.
Enrollment Policies demonstrates the configuration of the enrollment process and how to configure Windows components to use the AEC.
Clients briefly describes the update of the policy at the client side, in order to request a certificate over AEC.
Existent Active Directory Installation
In most cases, an active directory is already present. For several security mechanisms to be able to function properly, TLS must be active.
Configure the domain name at the ldap.server.host property of application.properties, where the active directory runs .
|
Active Directory Installation
Installation Steps
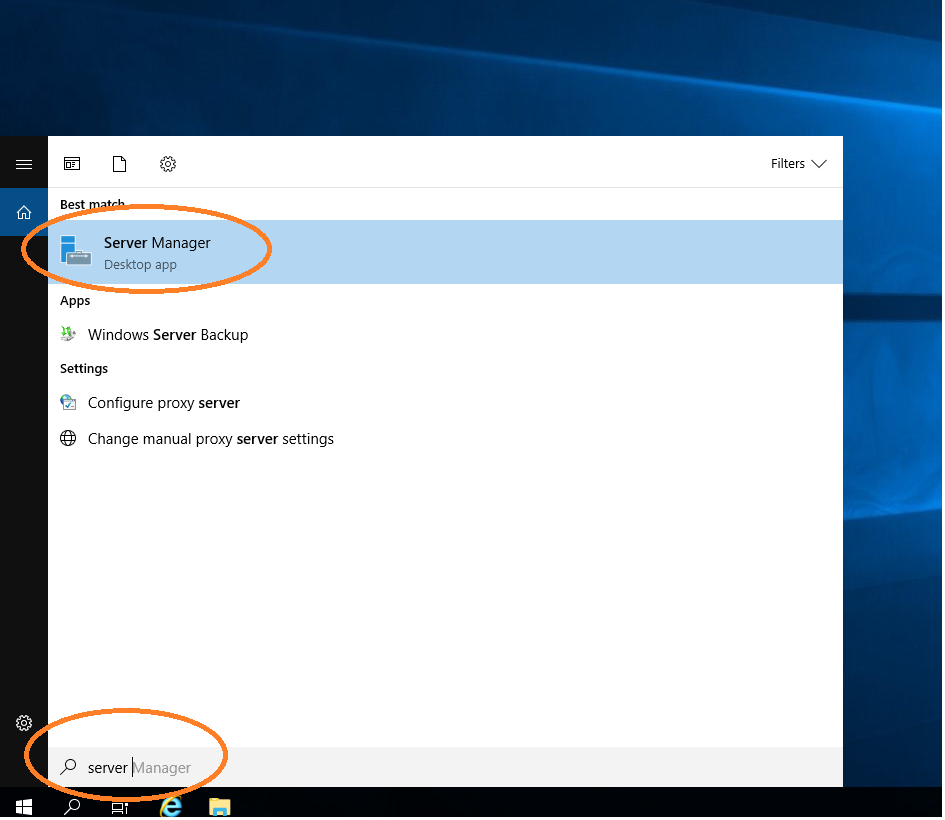
Add Active Directory
Choose Manage ~ Add Roles and Features.
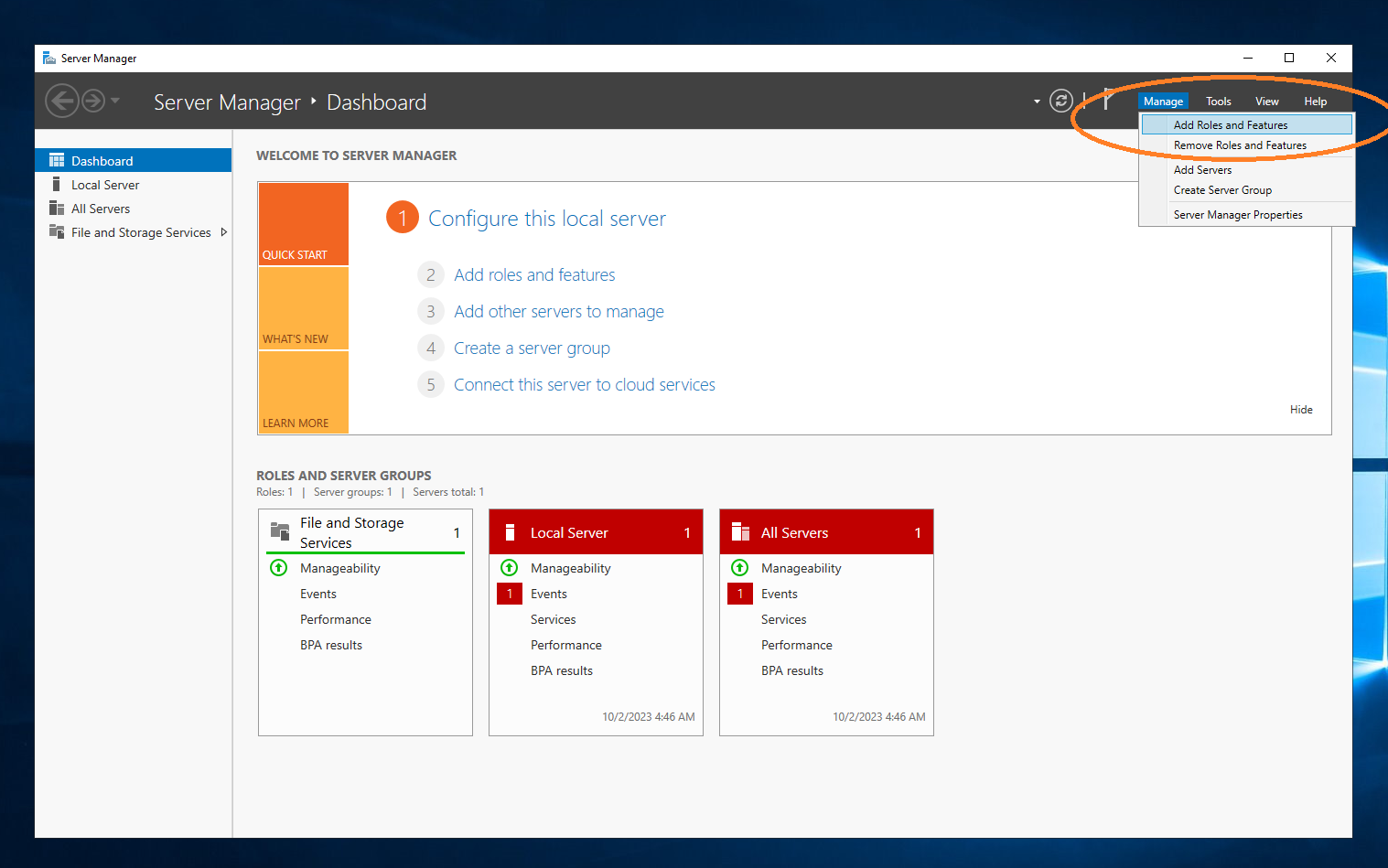
A configuration wizard starts. The first page of the wizard is shown below.
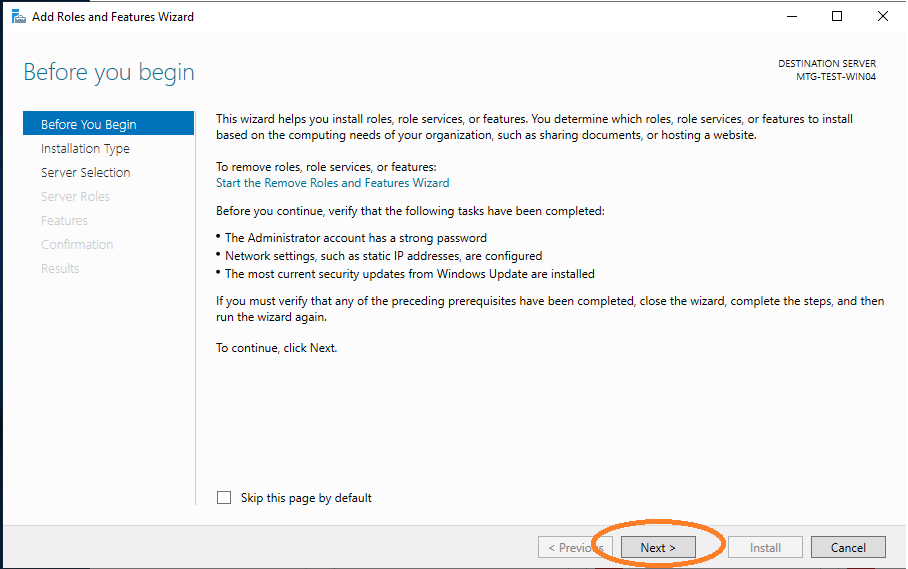
Choose the server where the active directory should be installed.
Choose the corresponding services for the active directory.
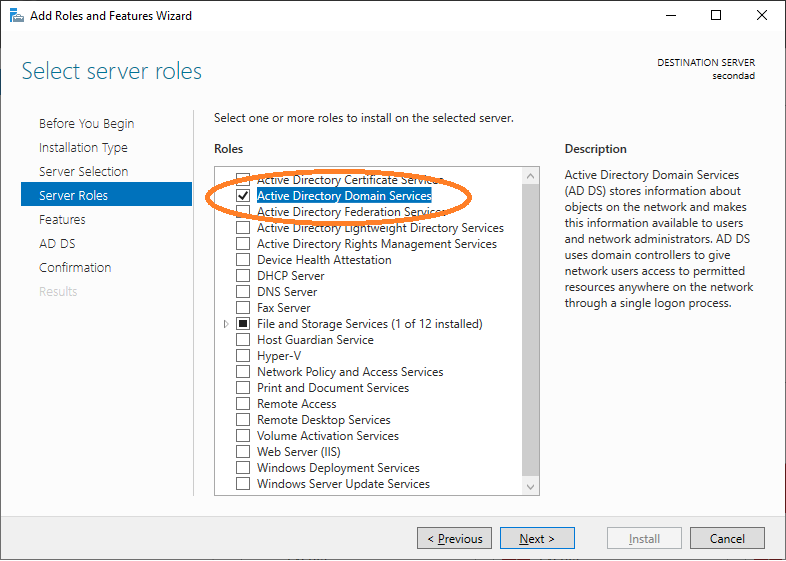
The Add Features window will appear. Click "Add Features".
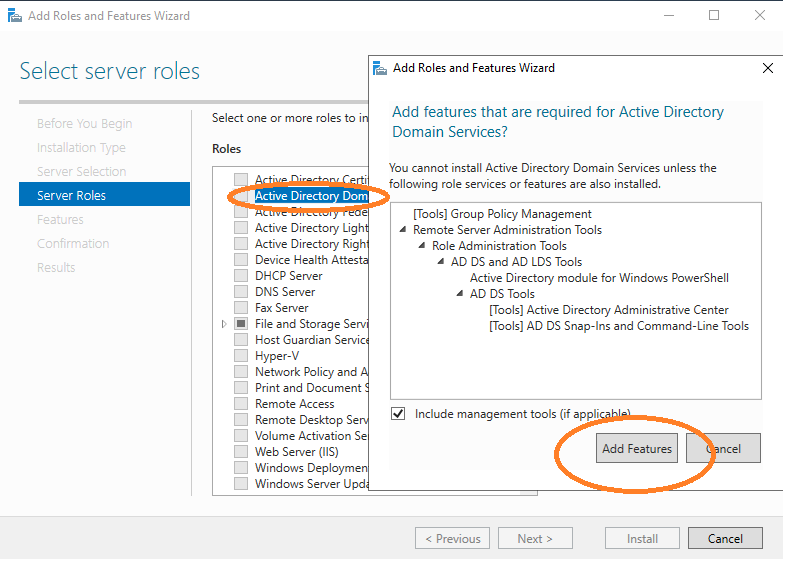
Click Next.
If it is not activated, activate Group Policy Management.
Click Next.
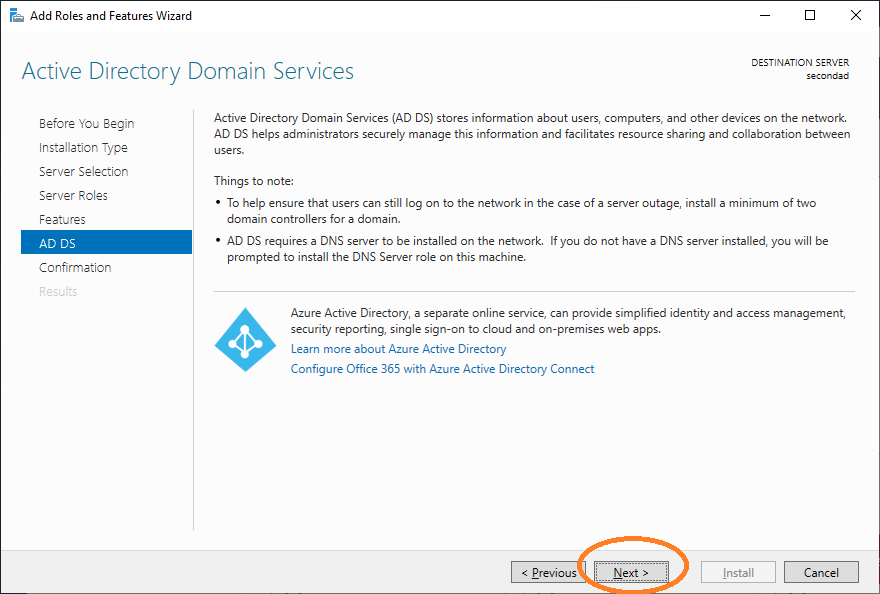
Click Install.
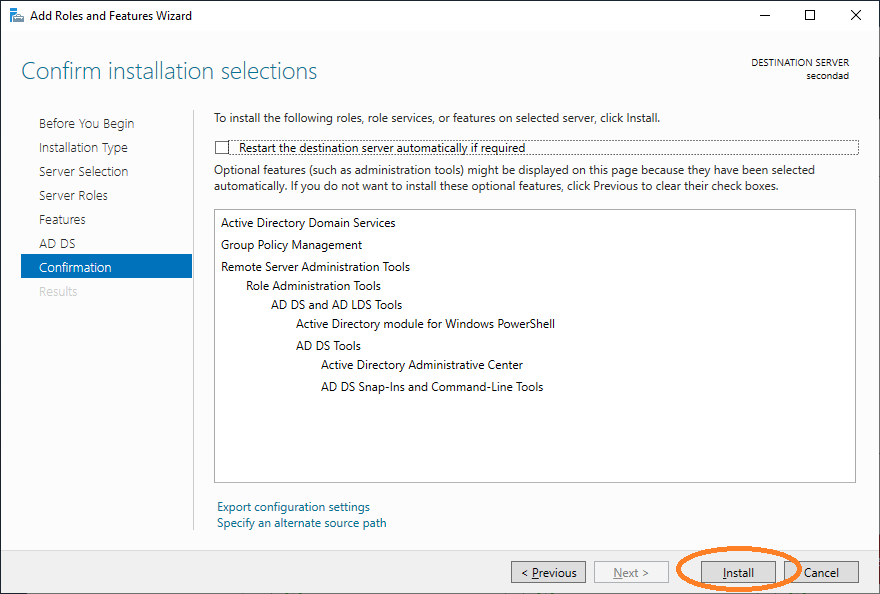
Close the dialog after successful installation.
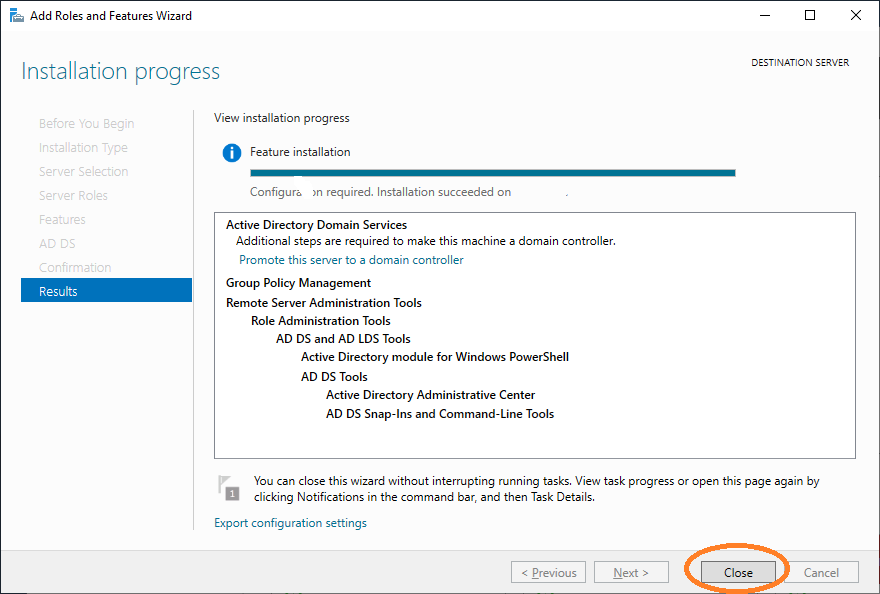
Configure the domain name where active directory runs at the
ldap.server.host property of application.properties. for example:ldap.server.host=ad.demo.mtg.
|
Promote to Domain Controller
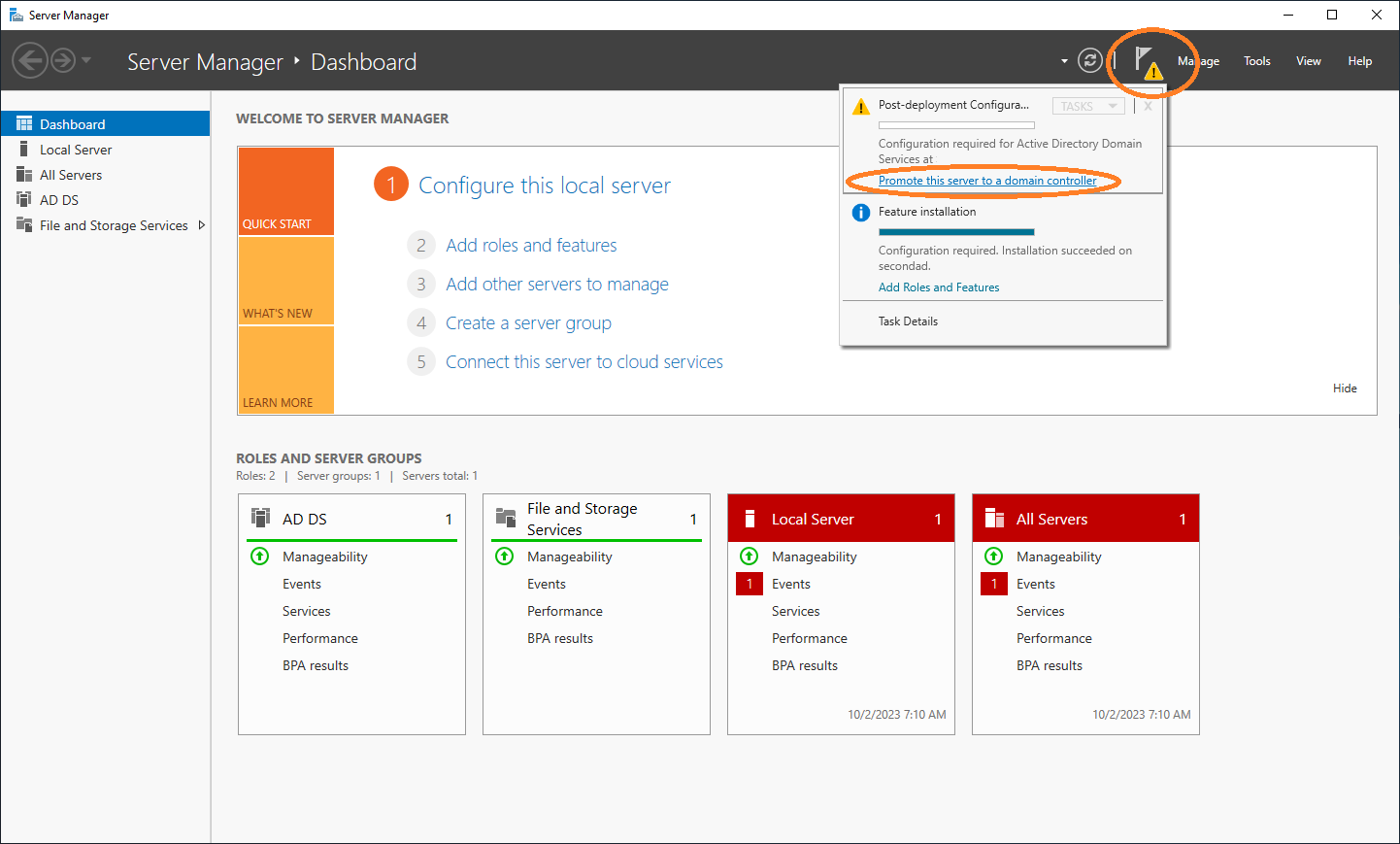
You can promote the server to a domain controller.
To do this, select Notifications ~ Promote this sever to a domain controller.
Choose 'Add a new forest' and provide the root domain name (in this example demo.mtg).
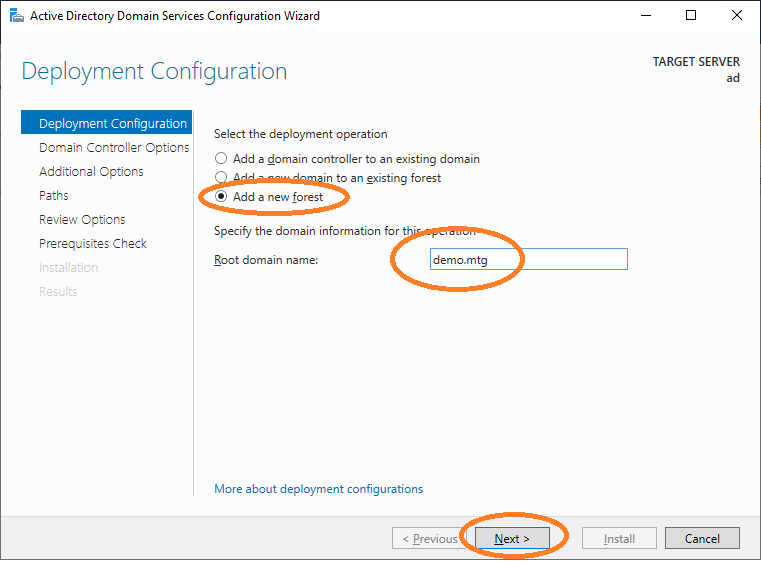
Provide a password and click Next.
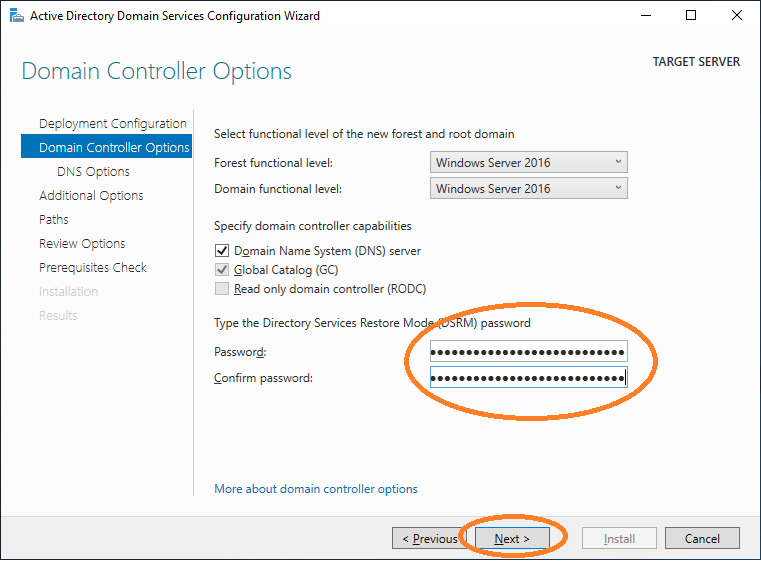
Proceed with the wizard.
Wait for the NetBIOS name to be resolved.
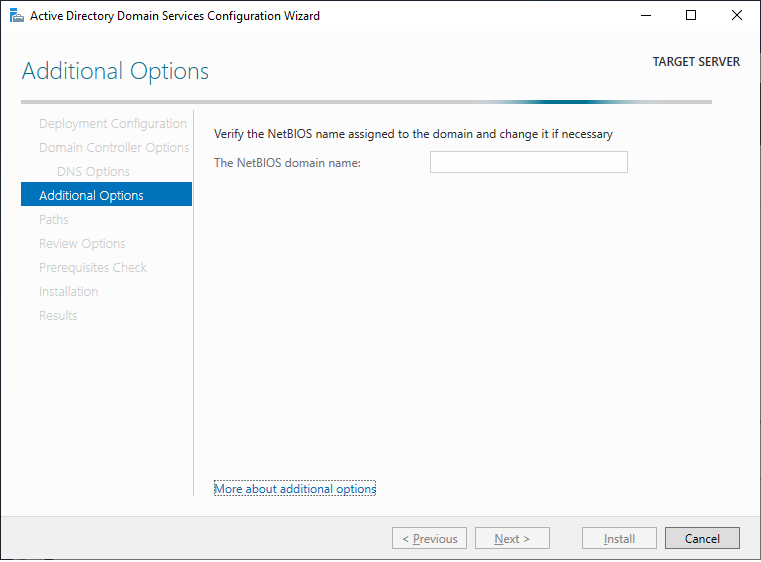
Provide the NetBIOS domain name.
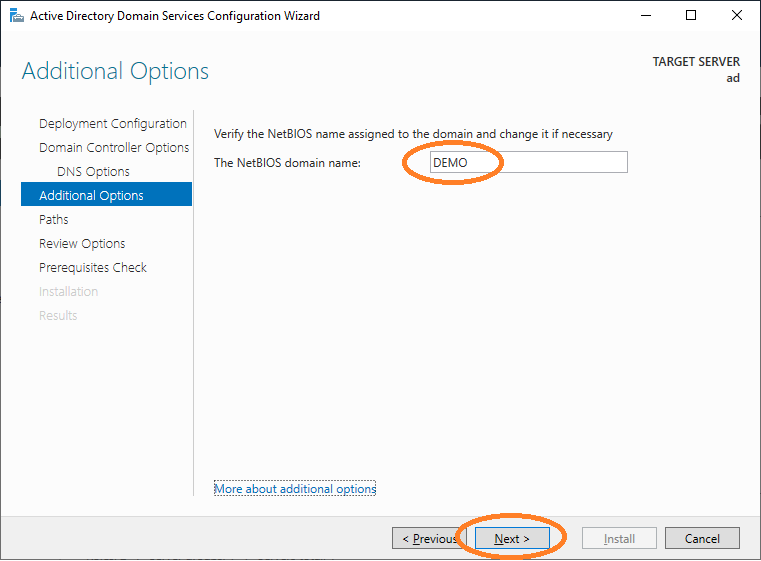
Proceed with the wizard.
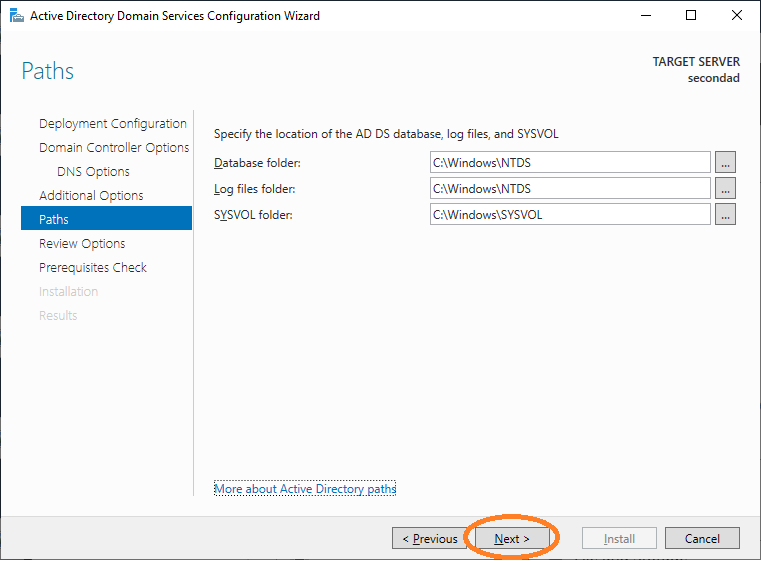
Proceed with the wizard.
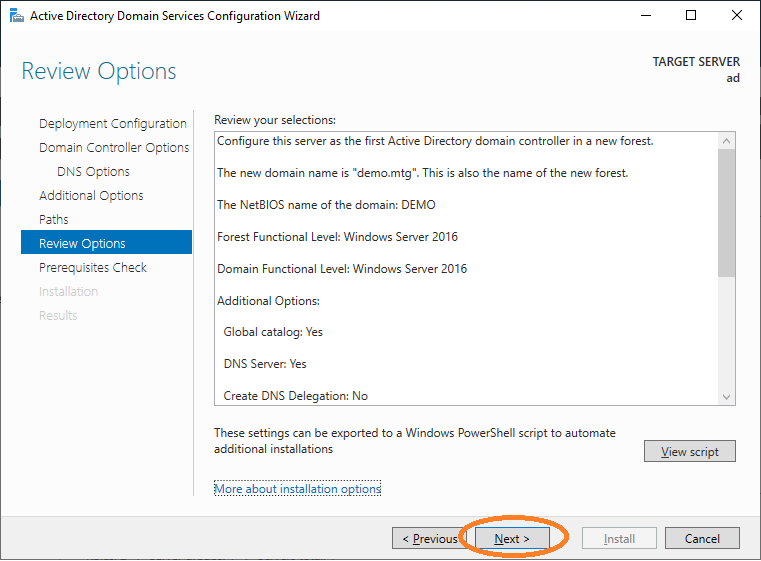
Finish the installation as shown below.
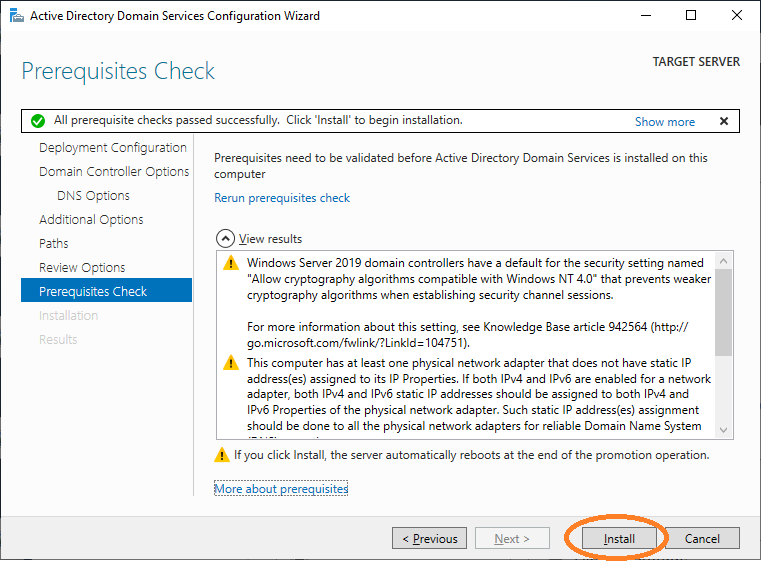
Your system with then restart.
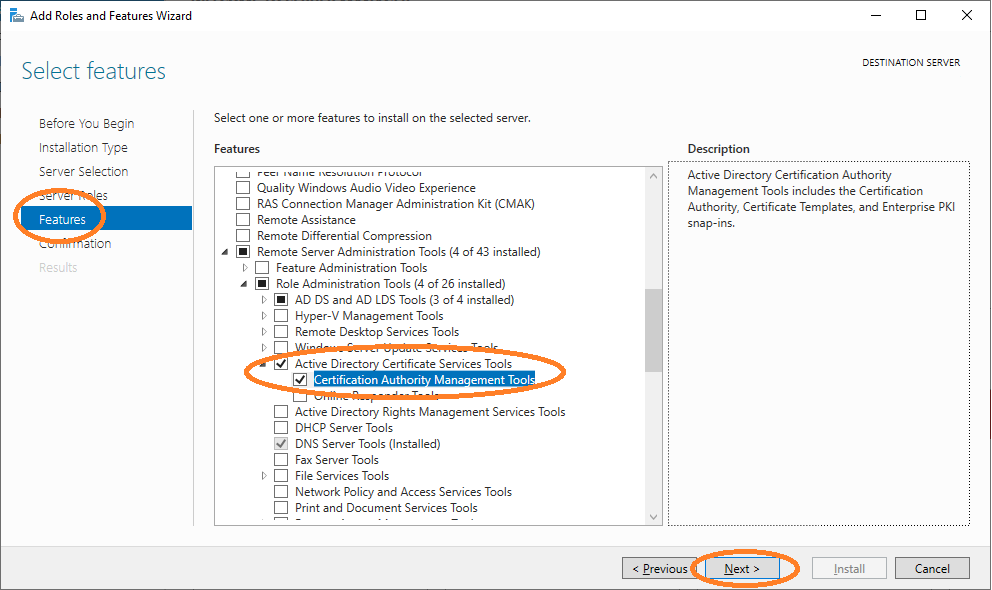
Add Certification Authority Management Tools
Under Server Manager ~ Manage ~ Add Roles and Features run the wizard as shown above, and now add Certification Authority Management Tools.
Configure TLS
Check that AD as an LDAP directory is running.
To do this, open a cmd Window and run ldp.
Provide the domain of the server and 389 as a port (389 is the default port of LDAP).
A connection should be established. See also Figure 22 on how to start the LDAP client tool and connect to server.
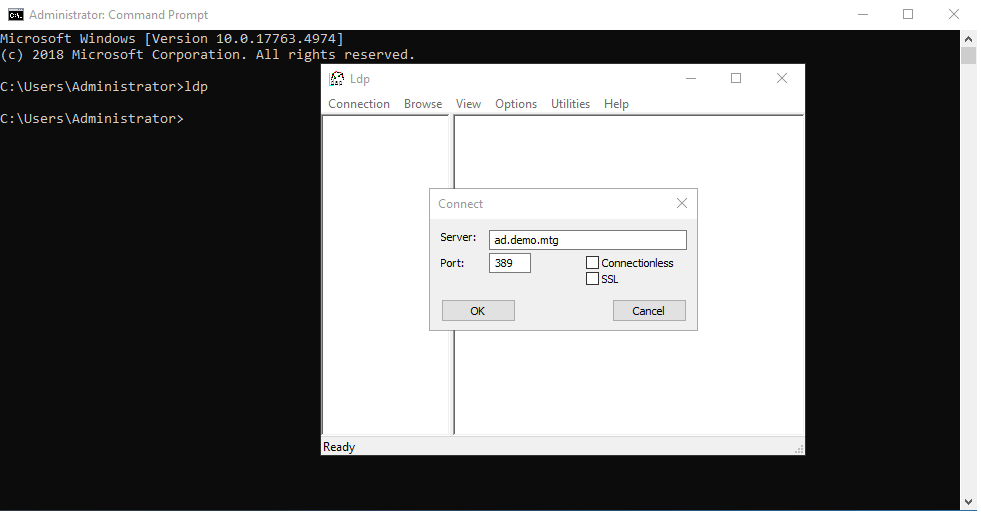
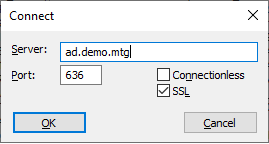
Trying the same for port 636 with SSL checked, will fail.
Copy the root CA and sub CA certificate on the server, and a PKCS12 file containing the keys and certificates of the active directory server.
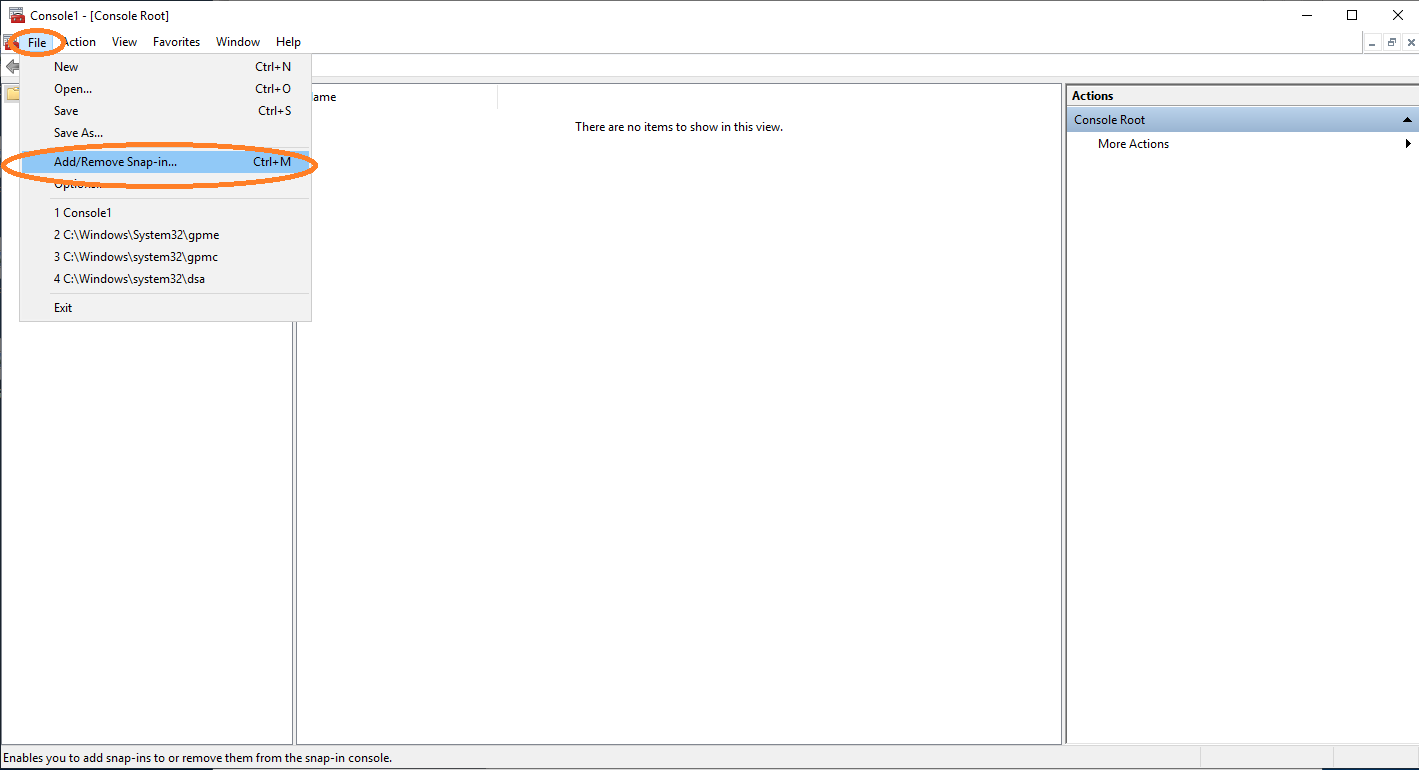
Open cmd and type mmc to get the Microsoft Management Console.
Click File and Add/Remove Snap in….
Select Certificates, click Add and then click OK.
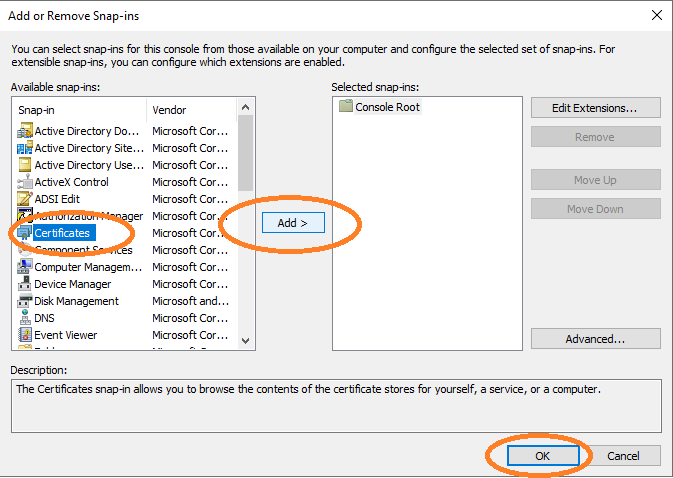
Choose Computer account and click Next.
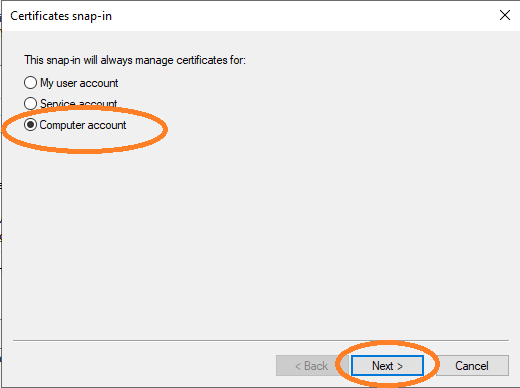
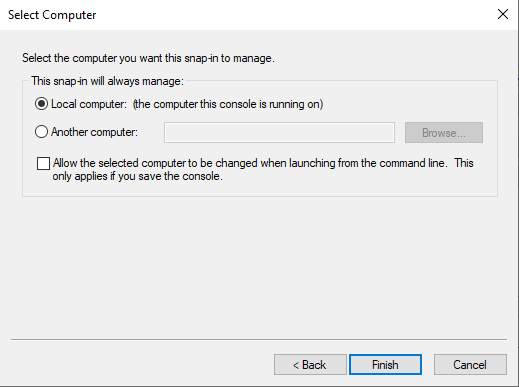
Choose Local computer and then Finish.
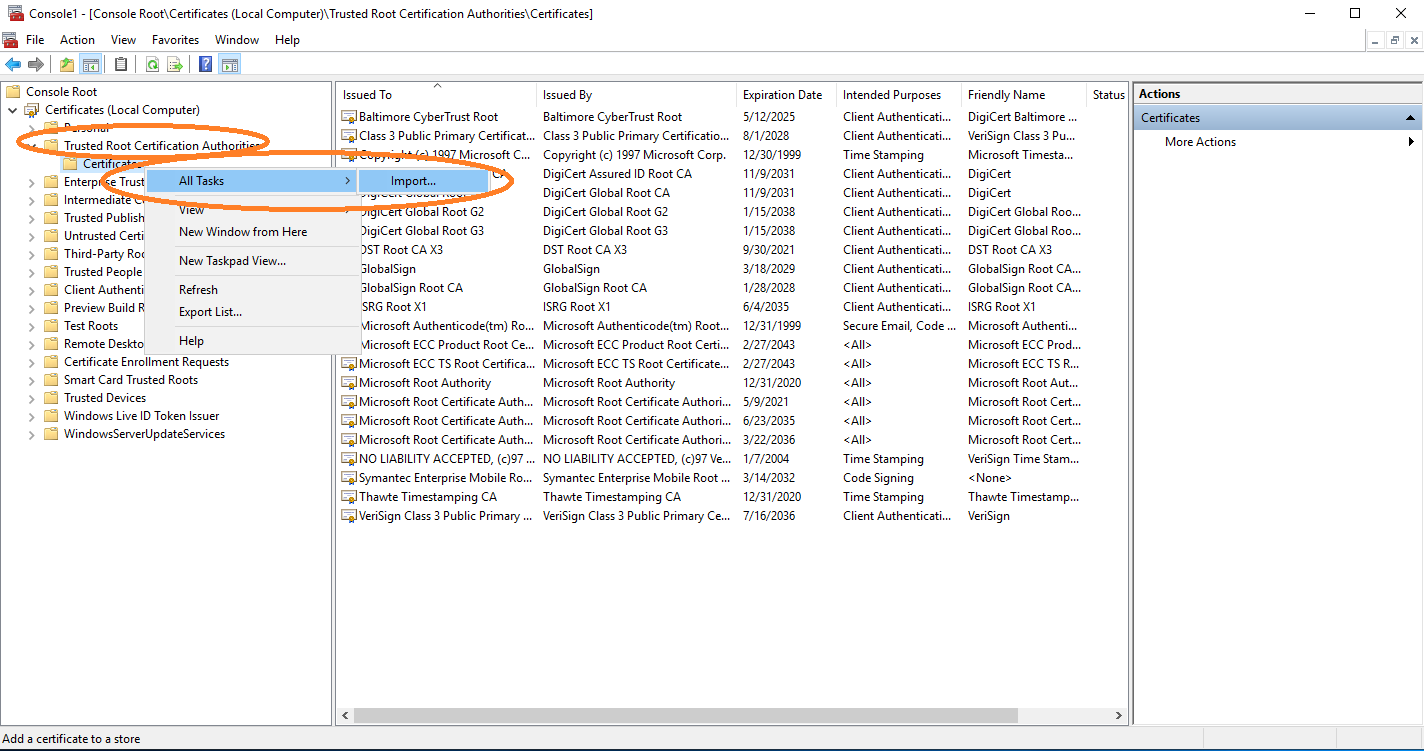
After adding the root, also add the sub CA certificate under Intermediate Certification Authorities.
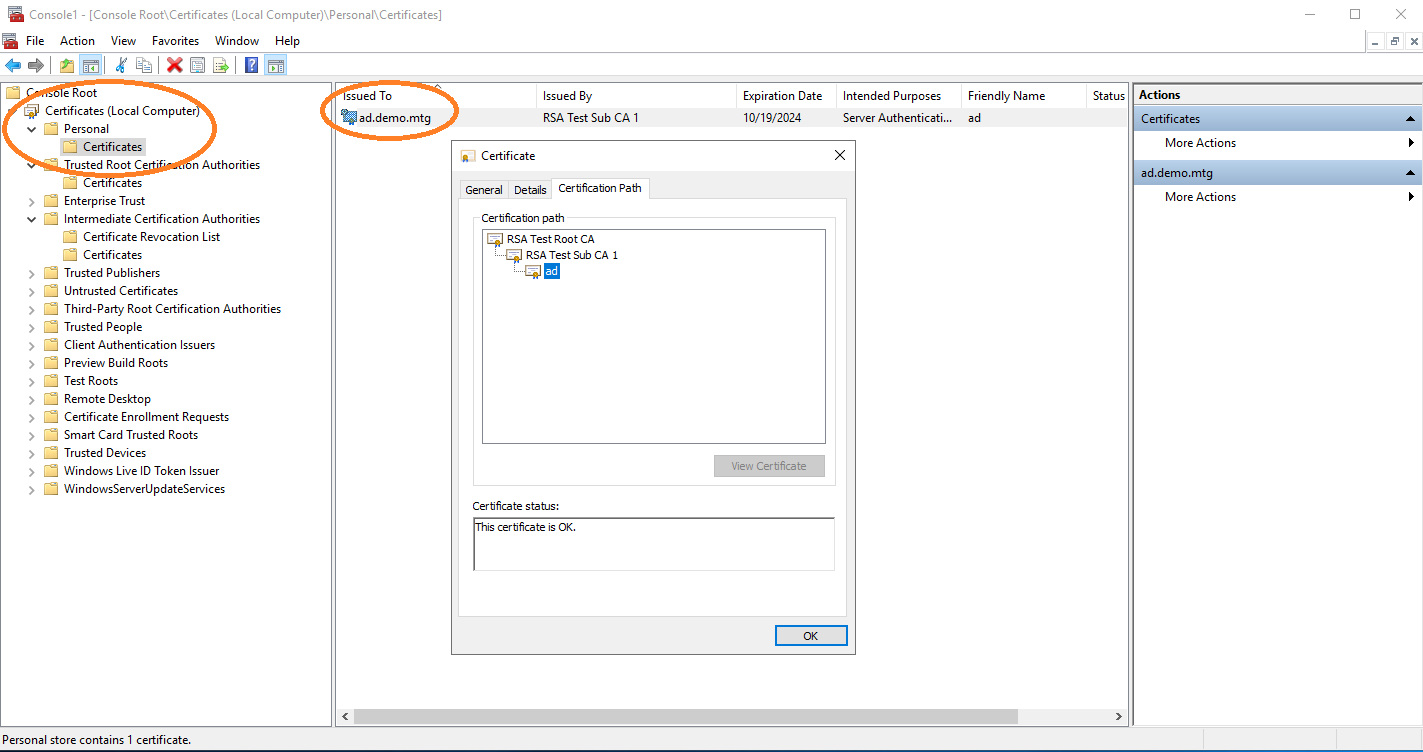
Finally import the private keys and certificates of the active directory server, under Personal.
You should now be able to connect to LDAP over TLS (Figure 23).
User Management
Add Users
For AEC to operate, two service accounts need to be created in the active directory.
The first is the service account aec-service.
This is the account of the AEC.
The second account is the aec-ldap-user.
This is an active directory user, needed by AEC to bind to active directory and perform LDAP operations.
Create Account aec-service
Under Tools ~ Activate Directory Users and Computers , add aec-service user.
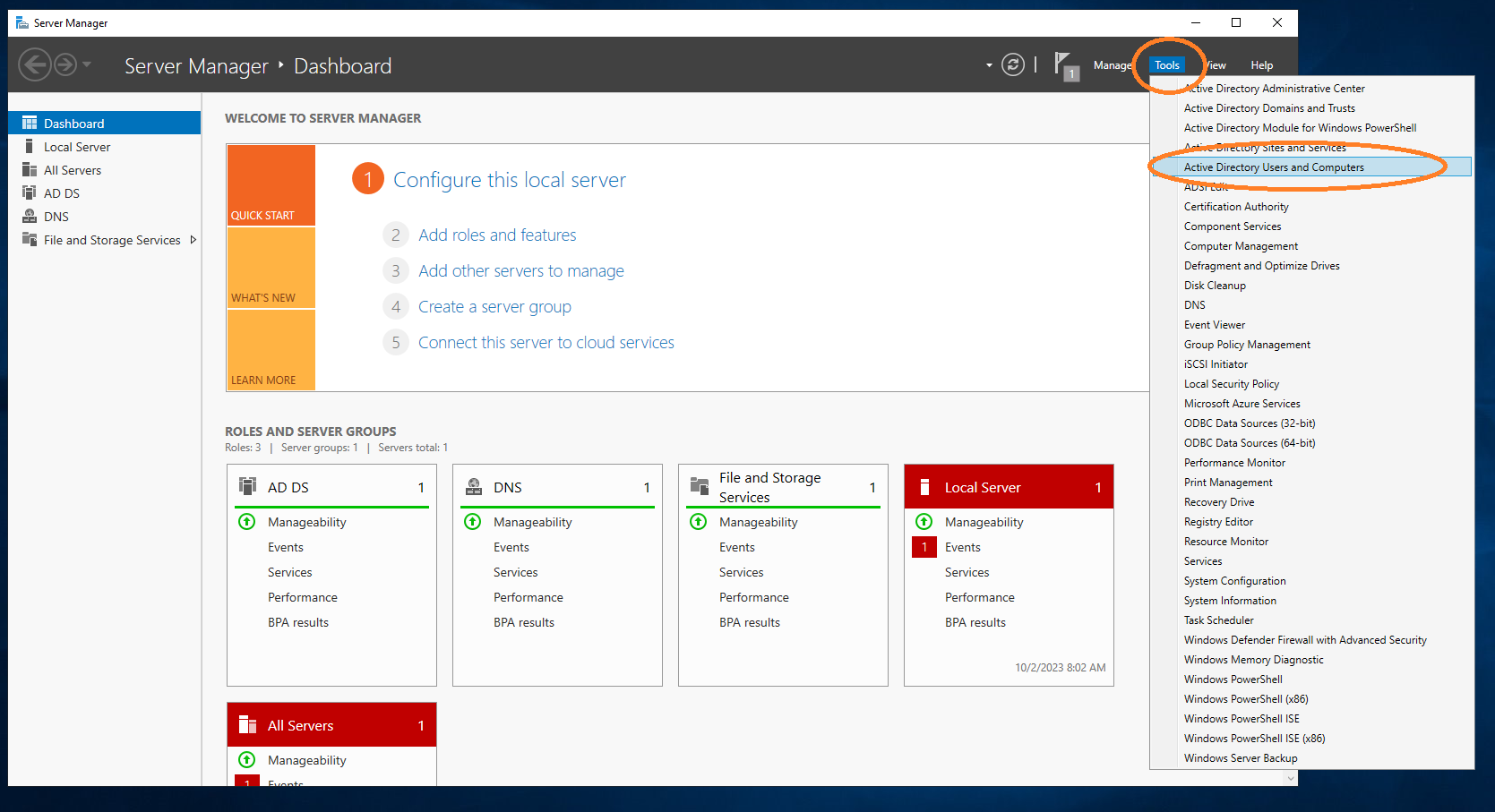
Go to Users.
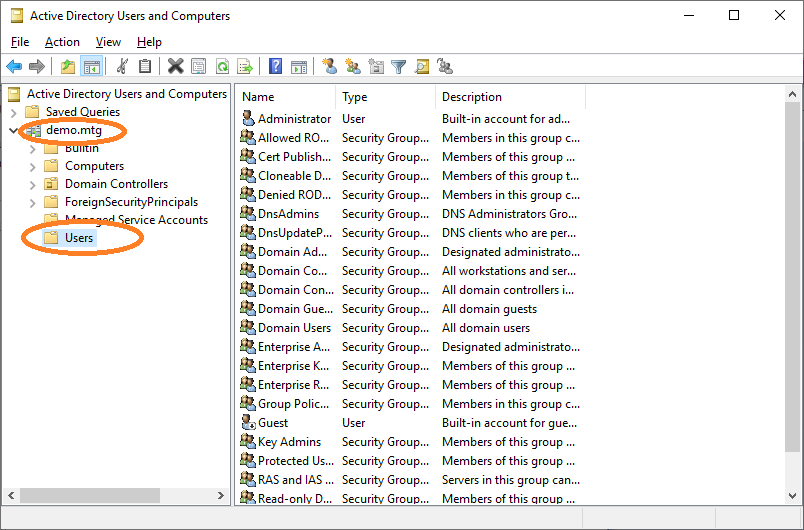
Add user.
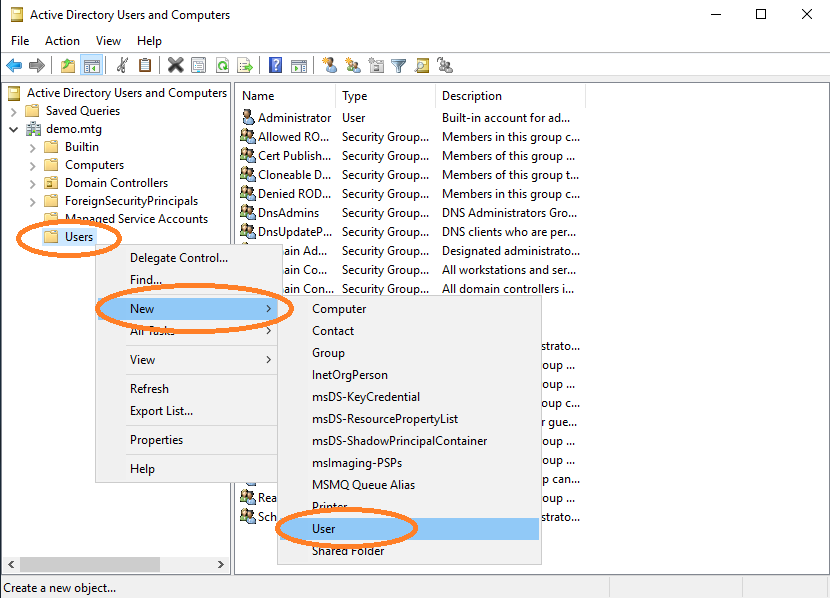
Provide a user logon name for this user. Choose aec-service.
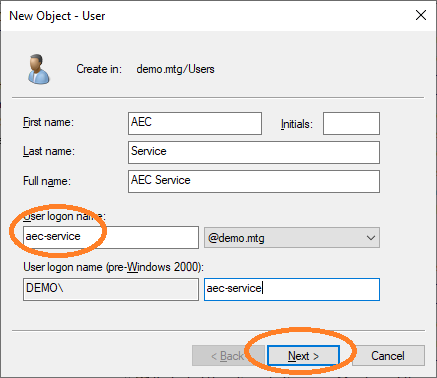
Provide the password for this user and choose Password never expires.
Finish the dialog to create the user.
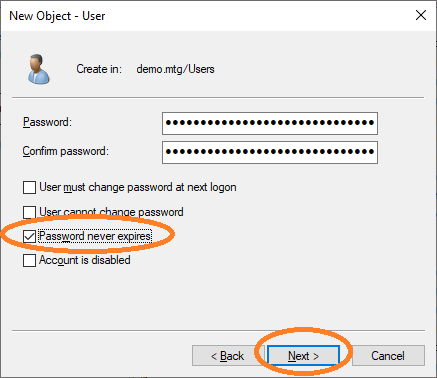
As a final step, activate support for AES128 and AES256 for this account.
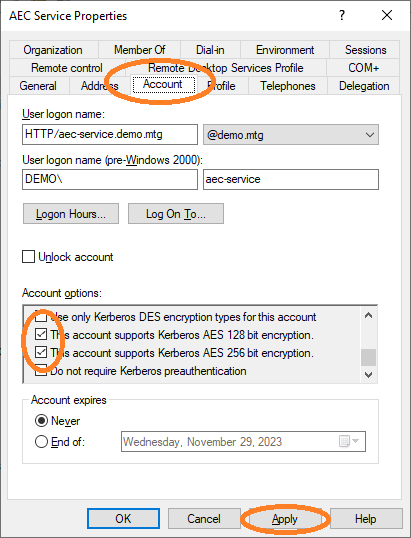
Then set the Service Principal Name (SPN) to the active directory for this user account:
setspn -s HTTP/aec-service.demo.mtg aec-servicewhich has the form HTTP/<FQDN where AEC runs>.
Configure the principal name of this user to the app.auth.service-principal property of application.properties. for example:app.auth.service-principal=HTTP/aec-service.demo.mtg.
|
The SPN of the user must match the domain name of the server running the AEC.
In this example, the domain name of the server running AEC must be set to aec-service.demo.mtg (see also Computers).
|
Then create a keytab file for this user to store its credentials.
ktpass -out application.keytab -mapUser aec-service@DEMO.MTG +rndPass -mapOp set +DumpSalt -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -princ HTTP/aec-service.demo.mtg@DEMO.MTG
General use:
ktpass -out <keytab-path> -mapUser <service-user-account-name>@<domain-name-in-upper-case-letters> +rndPass -mapOp set +DumpSalt -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -princ <service-principal-name>@<domain-name-in-upper-case-letters>
Configure application.keytab file to the app.auth.keytab-location
property of application.properties. for example:app.auth.keytab-location=application.keytab.
|
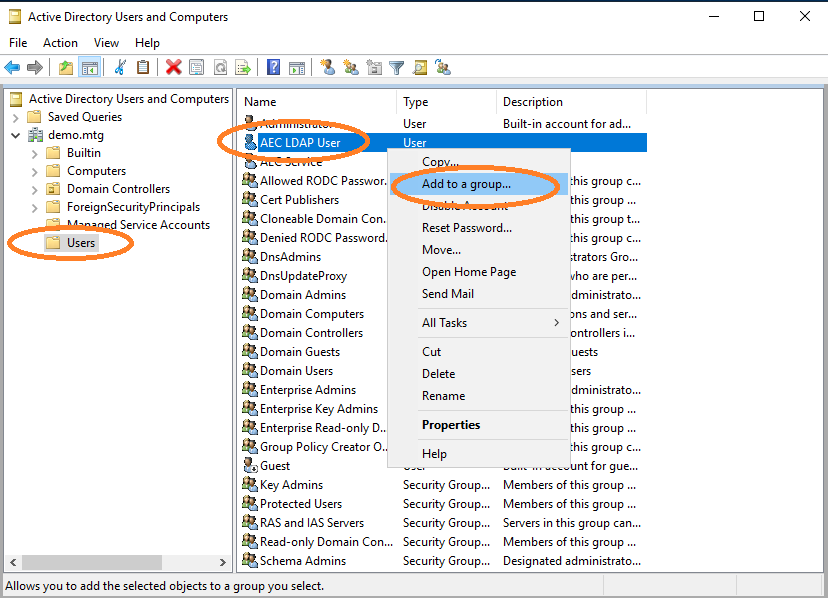
Create Account aec-ldap-user
Create a user performing the same steps as before, using aec-ldap-user as user logon name (do not set SPN or keytab yet, just create the user).
This user must be able to write certificates into the AD.
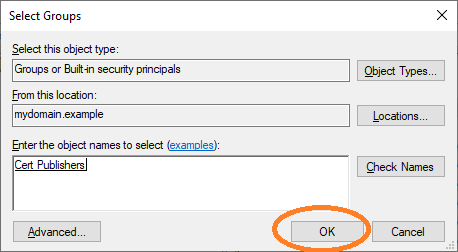
Therefore, this user must be added to the Cert Publishers group.
Navigate to aec-ldap-user and click Add to a group.
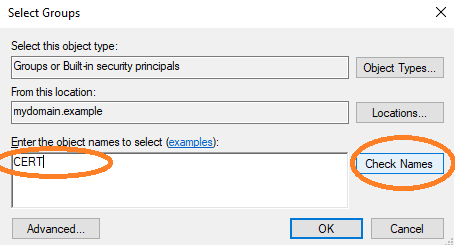
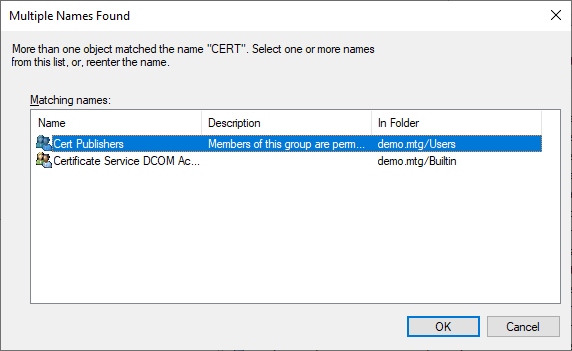
Finish the dialog by clicking OK.
Then create a keytab file for this user, to store its credentials.
ktpass -out aec-ldap-user.keytab -mapUser aec-ldap-user@DEMO.MTG +rndpass -mapOp set +DumpSalt -crypto AES256-SHA1 -pType KRB5_NT_PRINCIPAL -princ aec-ldap-user@DEMO.MTG
General use:
ktpass -out <keytab-path> -mapUser <ldap-user-account-name>@<domain-name-in-upper-case-letters> +rndPass -mapOp set +DumpSalt -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -princ <ldap-user-principal-name>
Configure aec-ldap-user.keytab file to the ldap.auth.keytab-location
property of application.properties. for example:ldap.auth.keytab-location=aec-ldap-user.keytab.
|
Configure the principal name of this user to the ldap.auth.service-principal property of application.properties,
for example:ldap.auth.service-principal=aec-ldap-user@DEMO.MTG.
|
Computers
Set Domain Name for the AEC
The computer where the AEC application runs must be made known to the Windows system. Go to DNS management.
Add a new host.
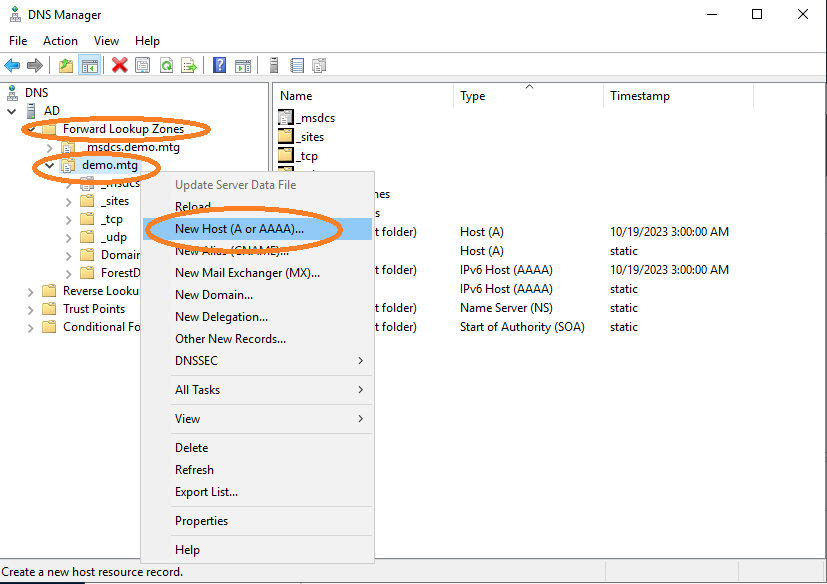
Provide a domain name for the IP where the AEC application runs, in this example at 198.51.100.90.
The name must be aec-service .
It is important that FQDN, SPN, and names are consistent to each other.
Here it is shown that the computer has been properly registered.
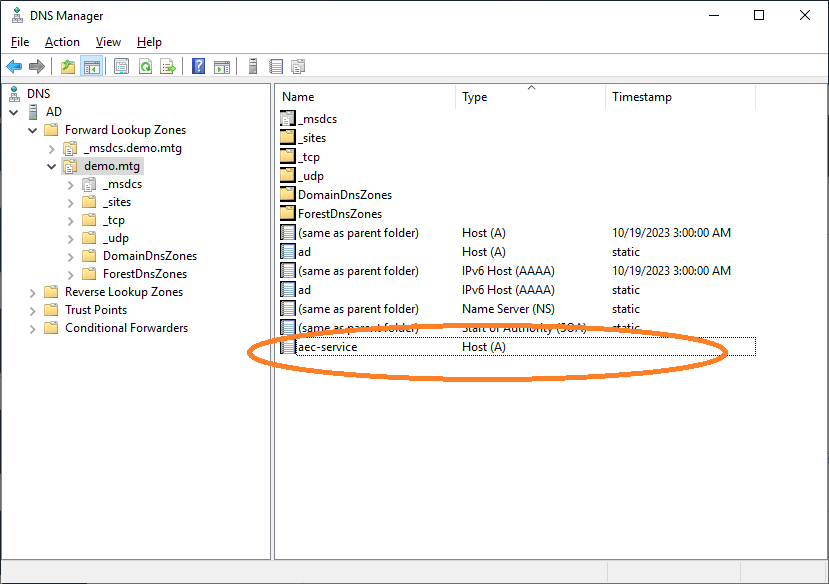
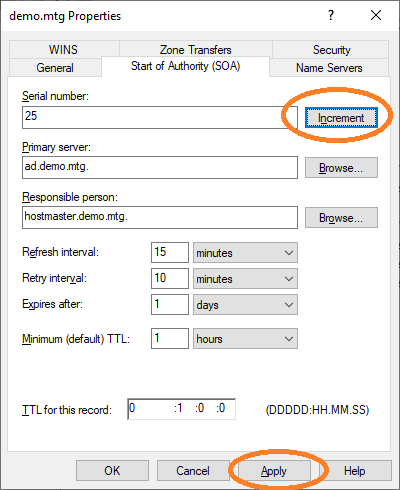
Finally, increment the Start of Authority and click Apply as shown below.
AEC
The AEC service must be able to verify and work with kerberos tokens that arrive from the various clients. In the previous section, the configuration of the name of the service was described. Additionally, a kerberos configuration file is necessary in order for AEC to be able to work with the kerberos protocol.
In Listing 1 the configuration file that is needed by the kerberos protocol is show.
The values in this file follow the configured domain demo.mtg of this document.
Configure the location of this file at the app.auth.krb5.conf`property of application.properties. for example:app.auth.krb5.conf=krb5.conf.
|
[libdefaults]
default_realm = DEMO.MTG
default_tkt_enctypes = aes256-cts aes128-cts
default_tgs_enctypes = aes256-cts aes128-cts
permitted_enctypes = aes256-cts aes128-cts
udp_preference_limit = 1
[realms]
DEMO.MTG = {
kdc = ad.demo.mtg
default_domain = demo.mtg
}
[domain_realm]
.demo.mtg = DEMO.MTG
demo.mtg = DEMO.MTGConfigure Templates
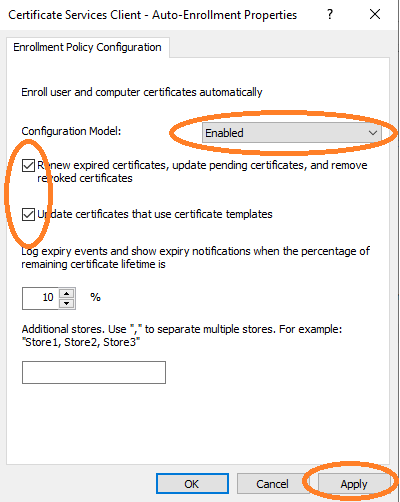
In this section, the setup of the templates for user and computer autoenrollment is described.
User Templates for Autoenrollment
Open cmd and type mmc to get the Microsoft Management Console (see Figure 24) and add Certificate Templates as shown below.
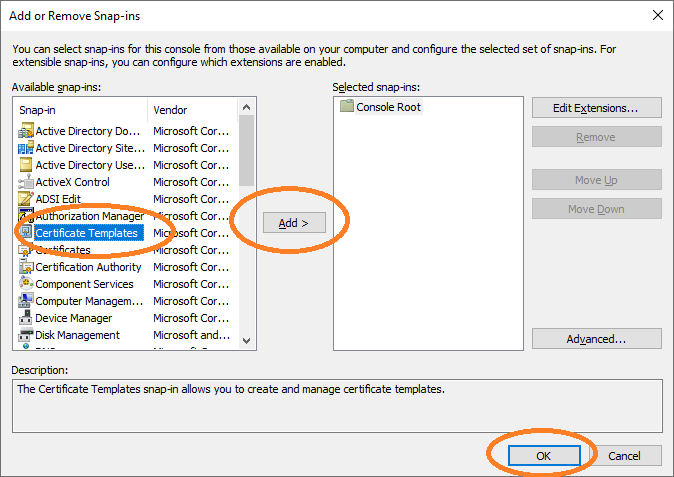
In the certificate templates view, duplicate the User template to retrieve a new template that you can configure for autoenrollment.
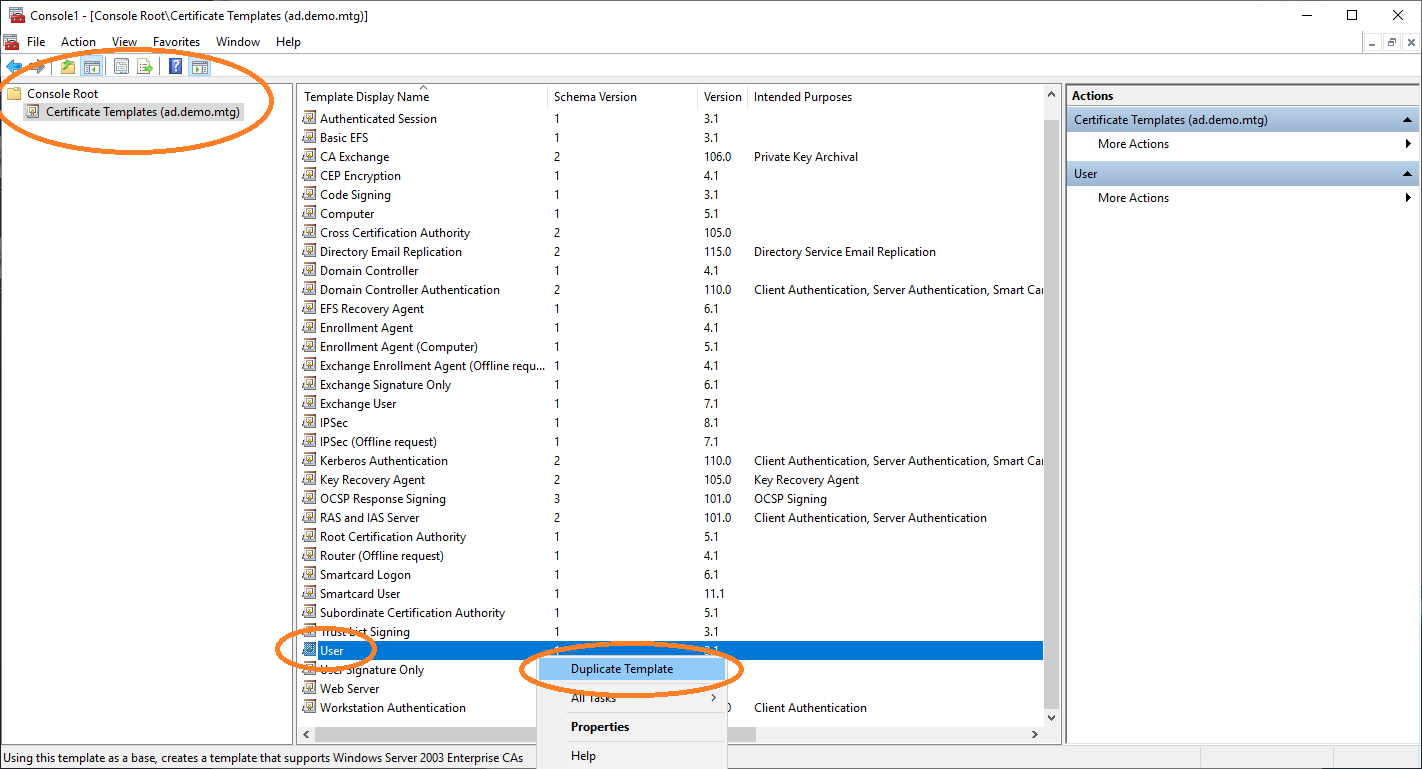
You must set the name of this new template, in tab General.
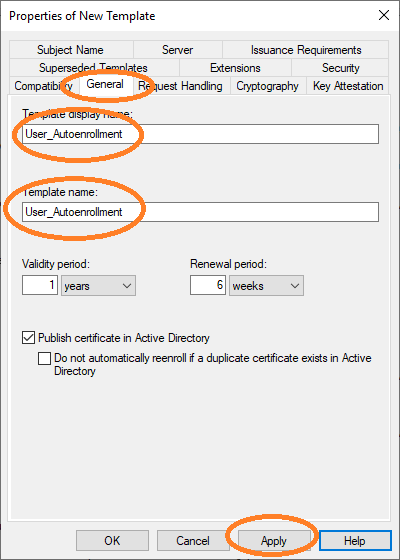
The template name User_Autoenrollment must be configured in the mapping.json file of AEC under certTemplates.
|
Then, allow autoenroll for a certain group or users.
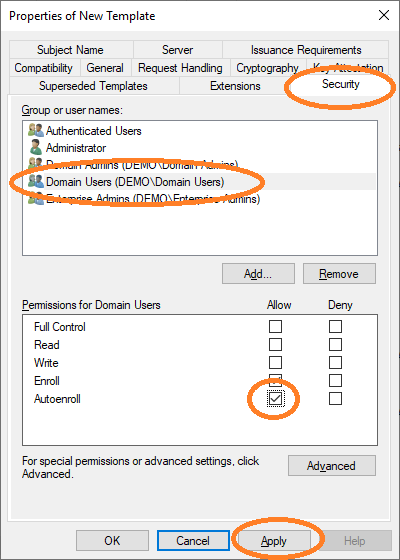
The new template is now listed.
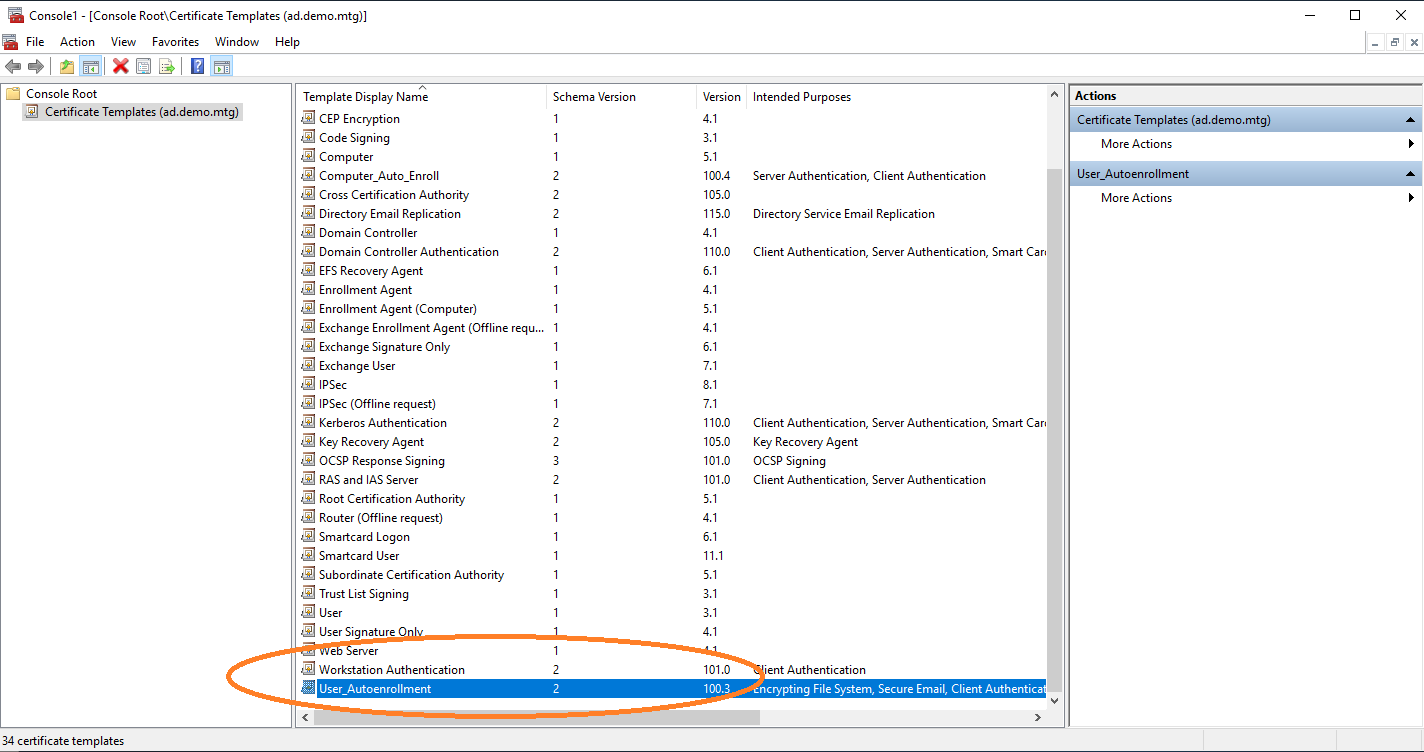
Computer Templates for Autoenrollment
Use the template named Computer for duplication and repeat the steps described in User Templates for Autoenrollment.
Enrollment Policies
You need to start AEC. For this step, it is required that the service is properly configured and is in operation.
Computer Configuration
To request certificates, windows clients query a policy server to receive information about the templates and location of the enrollment server.
In this section, the configuration of the location of AEC as a policy server is described.
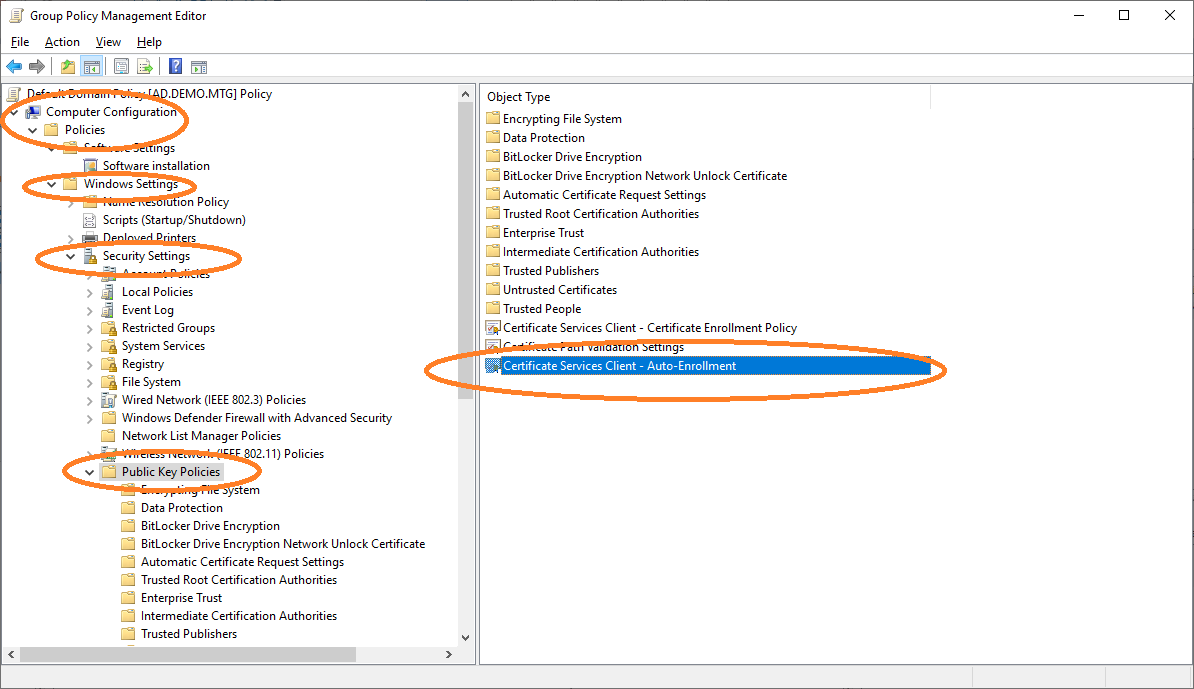
This configuration is performed under Group Policy Management.
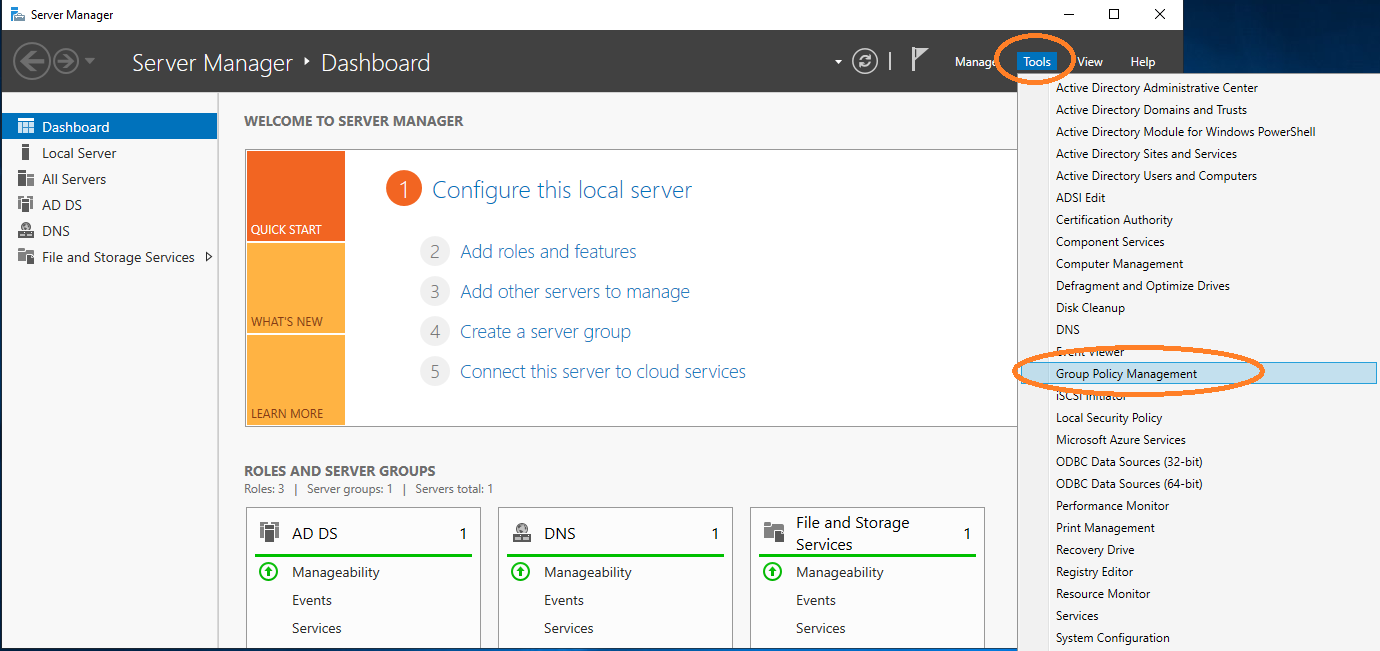
Edit The default policy of the domain.
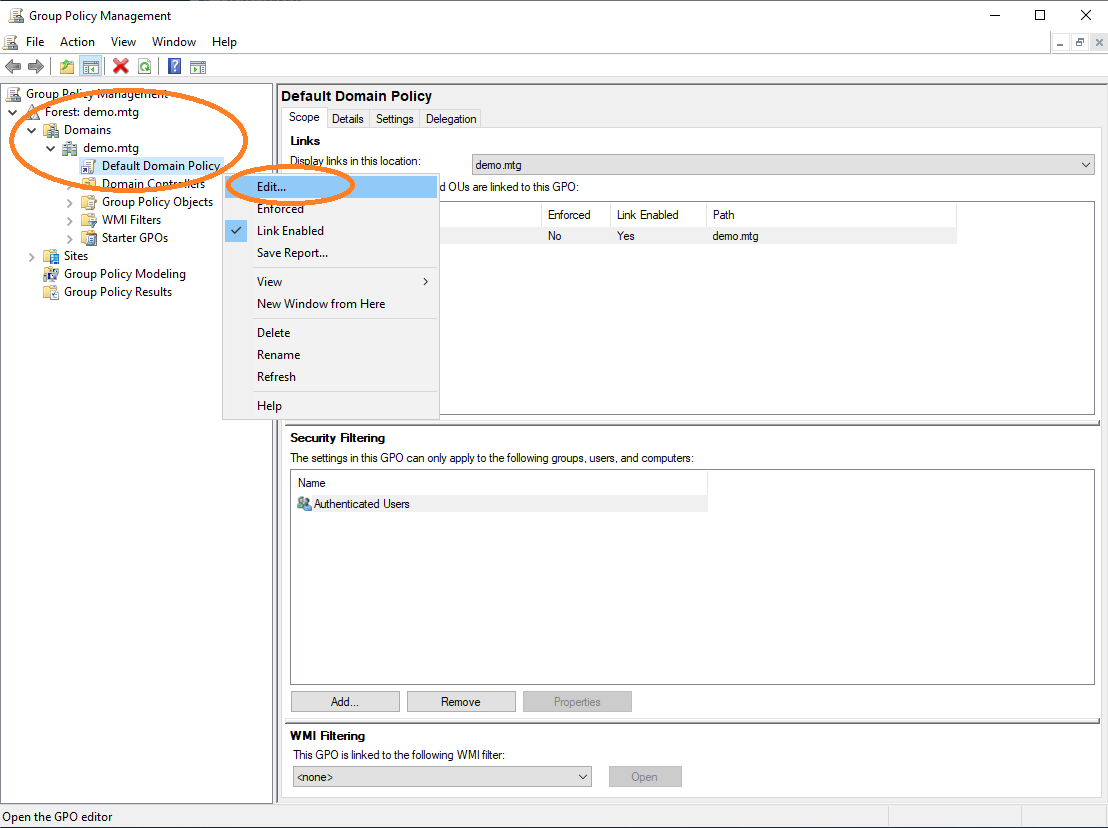
Choose the configuration of the certificate enrollment policy.
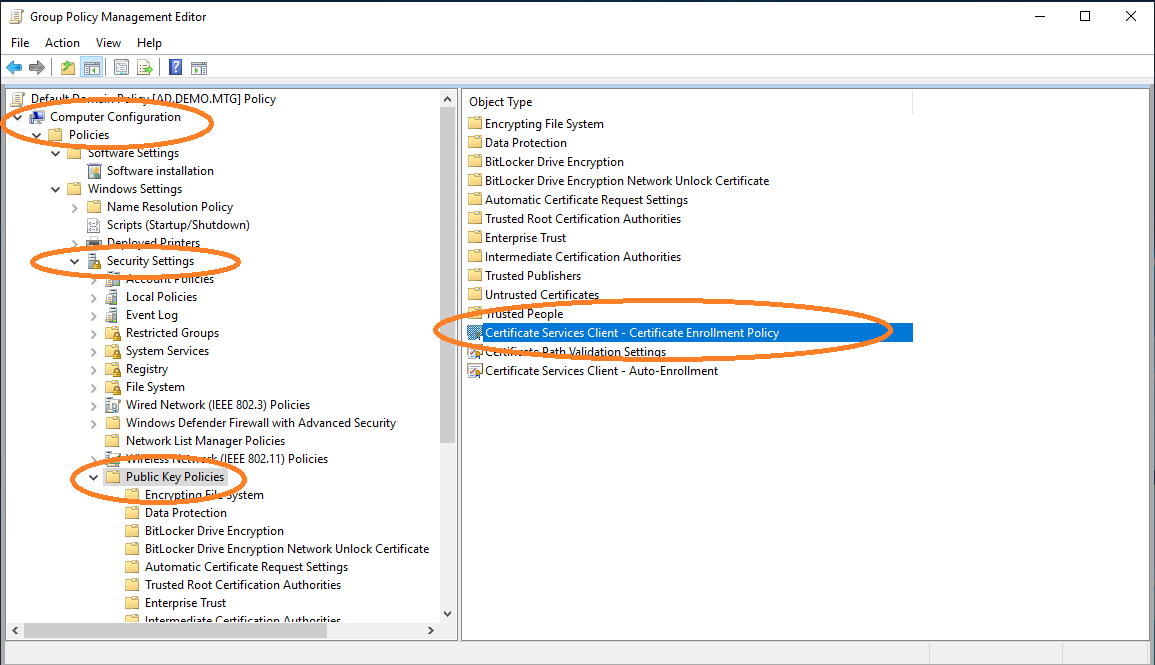
The AEC must be enabled and added as a new policy server.
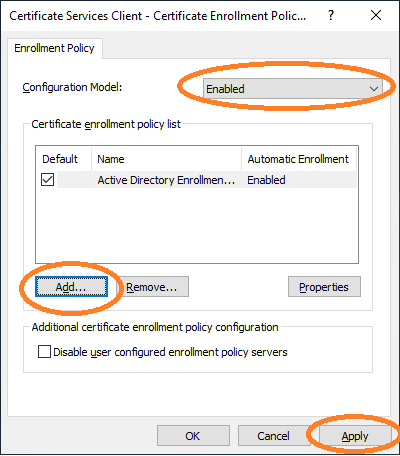
The URL of AEC must be entered. This URL can then be validated.
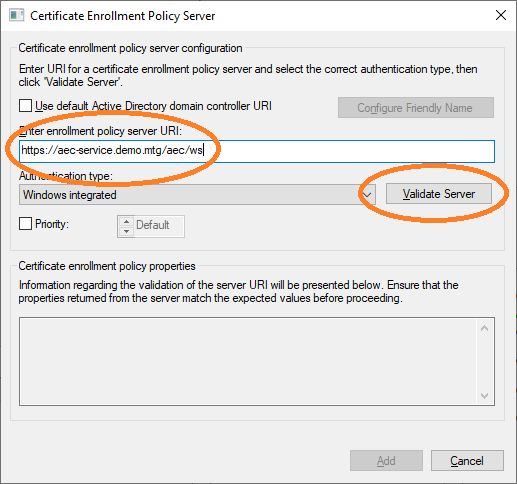
A successful validation is shown below.
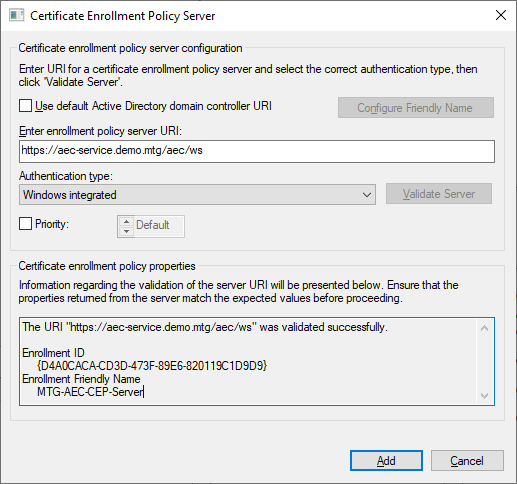
The newly configured policy server will then appear in the list of policy severs. It should be chosen as default certificate enrollment policy.
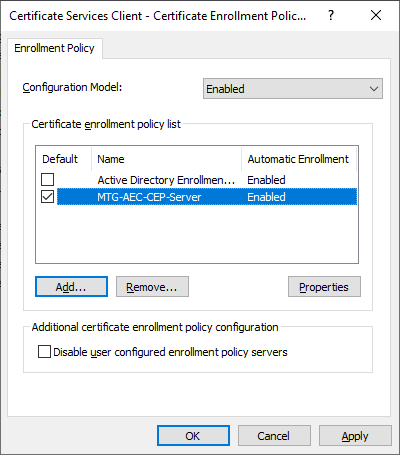
User Configuration
The steps are similar to the steps described in Computer Configuration and are not further described here.
Distribute Root and Sub CA Certificate
Import the root CA certificate into the policy, in order for it to be distributed to other clients. Edit default domain policy (see Figure 52) and import the root CA certificate.
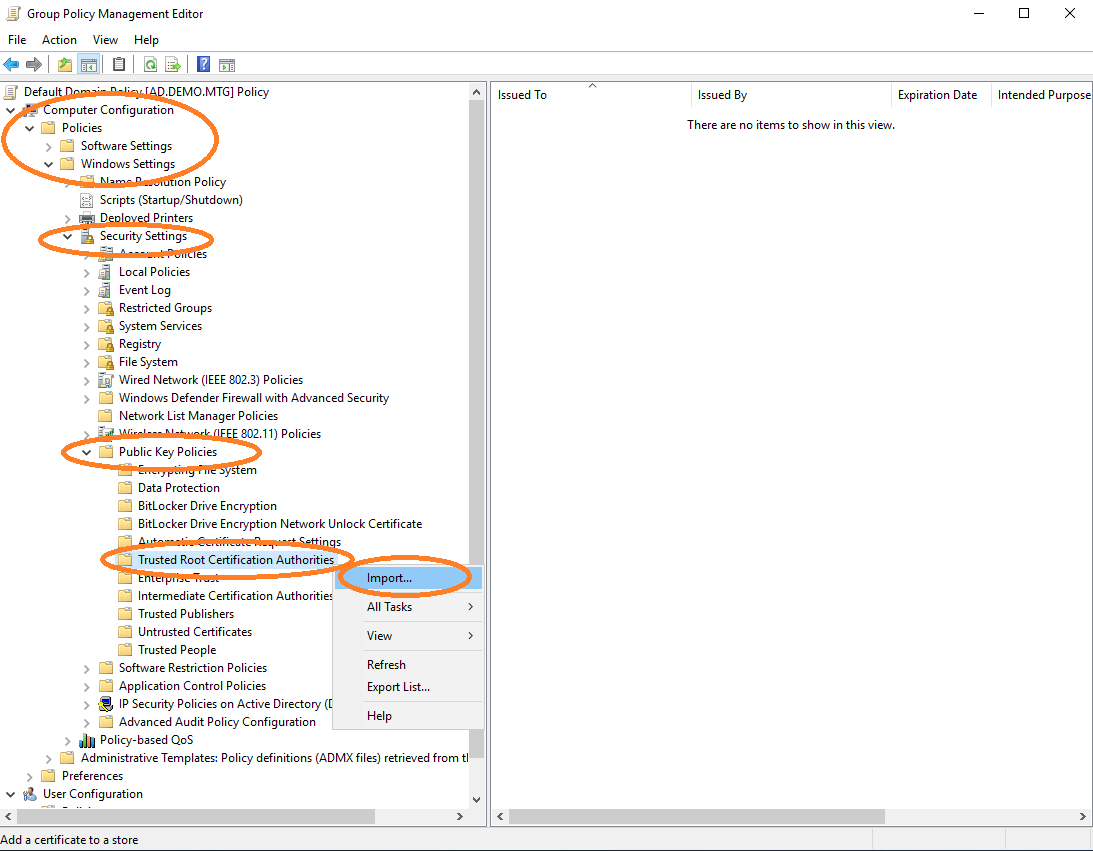
To import the sub CA certificate, perform the above under Intermediate Certification Authorities.
Clients
The server-side configuration is ready. You should also update the policy at the client-side, as shown below, in order to receive the newest policy containing the newly configured policy servers, templates, etc.
gpupdate /forceYou can also check whether the new policies are properly set:
certutil -policyserver * -policycachecertutil -f -user -policyserver * -policycacheThen request a new certificate for the user or computer you are working on.